DENIAL OF SERVICE (DoS)
Denial-of-service
(DoS)
attack
is an attempt to make a machine or network resource unavailable to
its legitimate users, such as to temporarily or indefinitely
interrupt or suspend services of a host connected to the Internet.
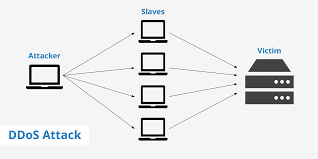
A
distributed
denial-of-service (DDoS)
is where the attack
source is more than one, often thousands of, unique IP addresses. It
is same to a group of people crowding the entry door or gate to a
shop or business, and not letting legitimate parties enter into the
shop or business, disrupting normal operations.
Outcome
-
Unusually slow network performance (opening files or accessing web sites)
-
Unavailability of a particular web site
-
Inability to access any web site
-
Dramatic increase in the number of spam emails received—this type of DoS attack is considered an e-mail bomb
-
Disconnection of a wireless or wired internet connection
-
Long term denial of access to the web or any internet services
If
the attack is conducted on a sufficiently large scale, entire
geographical regions of Internet connectivity can be compromised
without the attacker's knowledge or intent by incorrectly configured
or flimsy network infrastructure equipment.
Attack
techniques
A
denial-of-service attack is characterized by an explicit attempt by
attackers to prevent legitimate users of a service from using that
service. There are two general forms of DoS attacks: those that crash
services and those that flood services.
The
most serious attacks are distributed and in many or most cases
involve forging of IP sender addresses so that the location of
the attacking machines cannot easily be identified, nor can filtering
be done based on the source address.
Attack
tools
A
wide array of programs are used to launch DoS-attacks.
In
cases such as My Doom the tools are embedded in malware, and launch
their attacks without the knowledge of the system owner. Stacheldraht
is a classic example of a DDoS tool. It utilizes a layered structure
where the attacker uses a client program to connect to handlers,
which are compromised systems that issue commands to the zombie
agents, which in turn facilitate the DDoS attack. Agents are
compromised via the handlers by the attacker, using automated
routines to exploit vulnerabilities in programs that accept remote
connections running on the targeted remote hosts. Each handler can
control up to a thousand agents
In
other cases a machine may become part of a DDoS attack with the
owner's consent, for example, in Operation Paybac,k organized by the
group Anonymous. The LOIC has typically been used in this way. Along
with HOIC a wide variety of DDoS tools are available today, including
paid and free versions, with different features available. There is
an underground market for these in hacker related forums and IRC
channels.The attack using slowloris is shown below
(S)SYN
flood
A
SYN
flood
occurs when a host sends a flood of TCP/SYN packets, often with a
forged sender address. Each of these packets are handled like a
connection request, causing the server to spawn a half-open
connection,
by sending back a TCP/SYN-ACK packet (Acknowledge), and waiting for a
packet in response from the sender address (response to the ACK
Packet). However, because the sender address is forged, the response
never comes. These half-open connections saturate the number of
available connections the server can make, keeping it from responding
to legitimate requests until after the attack ends.



This comment has been removed by the author.
ReplyDeleteVery nice and informative blog, i really come to know something unique and new. Hope you will provide more information to us, we also provide digital marketing service including all tasks like: SEO, SEM, PPC, SMO, SMM, E-mail marketing, Webdesign and development. If anyone in need, feel free to contact us:
ReplyDeleteDigital marketing Company in Delhi
SMM Services
PPC Services in Delhi
Website Design & Development Packages
SEO Services Packages
Local SEO services
E-mail marketing services
YouTube plans
Digital Marketing Service in Delhi